Hollywood Hackers Vs. Reality
from the CIP-#1,831-for-why-the-internet-is-scary dept
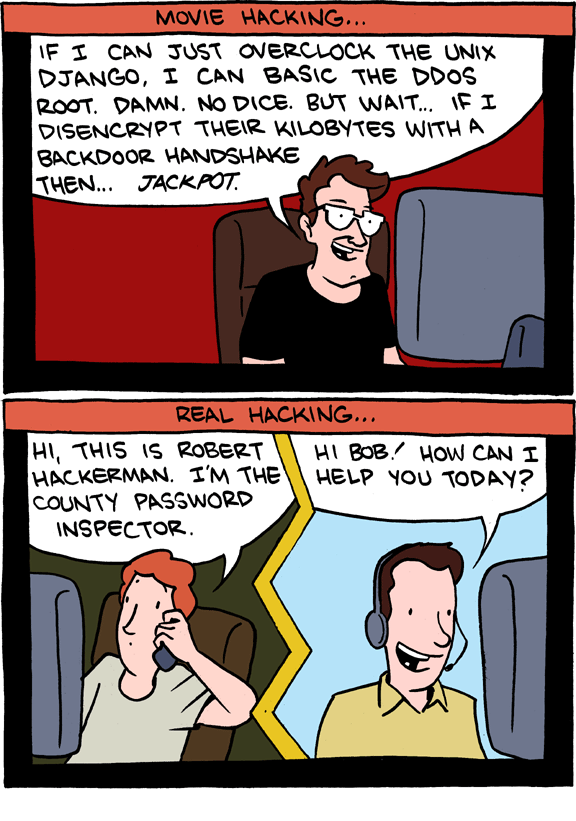
Perhaps no single "demographic" is more misunderstood (and feared -- especially post-SOPA debacle) by Hollywood than "The Hacker." In the hands of the movie machine, hackers are portrayed as fast-talking (and fast-typing) young men (and very occasionally, women) with unfortunate hairdos, huddled around multiple screens making use of thoroughly impractical GUIs, all the while spouting a confounding mixture of instantly-outdated slang and acronyms.Saturday Morning Breakfast Cereal breaks this down in an incredibly concise and incredibly awesome two-panel comic:

Thank you for reading this Techdirt post. With so many things competing for everyone’s attention these days, we really appreciate you giving us your time. We work hard every day to put quality content out there for our community.
Techdirt is one of the few remaining truly independent media outlets. We do not have a giant corporation behind us, and we rely heavily on our community to support us, in an age when advertisers are increasingly uninterested in sponsoring small, independent sites — especially a site like ours that is unwilling to pull punches in its reporting and analysis.
While other websites have resorted to paywalls, registration requirements, and increasingly annoying/intrusive advertising, we have always kept Techdirt open and available to anyone. But in order to continue doing so, we need your support. We offer a variety of ways for our readers to support us, from direct donations to special subscriptions and cool merchandise — and every little bit helps. Thank you.
–The Techdirt Team


Reader Comments
Subscribe: RSS
View by: Time | Thread
[ link to this | view in chronology ]
I love those thoroughly impractical GUIs. They're awesome. But they also point out that the hacker characters in movies are not only good at every type of hacking, cracking, and phreaking (which is unlikely), but they're also so talented in multimedia design that they could probably get better paying jobs doing freelance design while still able to choose their clients ethically and tell off corporate would-be clients.
At least the movie Hackers did show Johnny Lee Miller's character using social engineering to get access to the television station's network.
[ link to this | view in chronology ]
[ link to this | view in chronology ]
Re:
[ link to this | view in chronology ]
Re: Re:
[ link to this | view in chronology ]
http://xkcd.com/538/
[ link to this | view in chronology ]
Re:
Hmm, maybe I didn't think that one all the way thru.
[ link to this | view in chronology ]
Re: Re:
[ link to this | view in chronology ]
Re: Re: Re:
Heh. Back in the day I was co-admin for a Novell 3.12 corporate network and we did a password security check. "fuckyou" was the forth most used password, after "password", "123456" and "letmein". We quickly instituted monthly password changes with no repeats, but that really didn't make the network much more secure since 90% of the users wrote their passwords on Post-Its on their cubicle walls or top desk drawer.
[ link to this | view in chronology ]
Re: Re: Re: Re:
password1
password2
password3
password4
...
So then you really ramp up the security and insist on mixed case with mandatory punctuation characters ...
%Password1
%Password2
%Password3
%Password4
...
[ link to this | view in chronology ]
Re: Re:
"Password."
"Yes, tell us your password!"
"Password."
Continue until you determine Who's on first.
[ link to this | view in chronology ]
Tim, you forgot something...
[ link to this | view in chronology ]
Re: Tim, you forgot something...
[ link to this | view in chronology ]
Re: Re: Tim, you forgot something...
The early hacker movies it was ok. I mean the 80s and early 90s so few people had computers that you could make up just about anything and someone would believe it. There was even a certain charm to the sillyness of it.
Now it just comes across as being very sad that anyone is so computer illiterate.
[ link to this | view in chronology ]
Re: Re: Tim, you forgot something...
And here I was wasting my time with C++, Perl, Python, Assembler, Ruby and all those other allegedly real computer languages. I feel soooooooooo depressed!
[ link to this | view in chronology ]
Reminds me of the last time I watched Independence Day (was like 2 months ago in a tedious day I watched like 25 mins of it): the spaceship had seats that were ergonomically designed for humans and came with seatbelts. Convenient. Computer has exactly the software required for the activity and nothing else. Convenient. Thousands of terabytes are transferred in a very short time despite physical limitations but when there's 1% left and the bad guys come in it slows down insanely. Convenient.
At least the hacking/technological movies provide us some quality comdedy ;)
[ link to this | view in chronology ]
Re:
I call them unintentionally funny movies. Mission Impossible 2 comes to mind. Watched that on a flight from US to UK ... people around me were really confused why I was laughing so much.
[ link to this | view in chronology ]
Re:
[ link to this | view in chronology ]
Re:
Not that I think Independence Day is an especially intelligent movie, but I don't think it should be criticized unfairly.
The fighter that Will flew was the one that crashed many years and which the scientists had been rebuilding. It would make sense that they would install seats designed for humans so that when they figured out how to make it go, a human could pilot it. We're never shown the interior of an untouched alien fighter. For all we know, it might not have even had seats originally.
As for the amount of information transferred; I forget, does it ever explicitly mention/show how much data is being transferred? I only remember seeing a progress bar. If the amount wasn't stated, it's possible that they were only transferring a few megs.
[ link to this | view in chronology ]
Re: Re:
I criticise it as being a naked rip-off of V (by way of Childhood's End) and War Of The Worlds, with illogical plot points shoehorned in for no real reason (the "virus" angle only being there to homage Wells, for example, even though there's no logical reason it should work).
It's a brain-dead special effects movie that's only there to show some spectacular footage of things being blown up. A highly entertaining one, admittedly, but still...
[ link to this | view in chronology ]
Re:
Actually I always thought that was realistic. After all, they're using Windows aren't they?
[ link to this | view in chronology ]
Why bother hacking code...
One of the fundamental principles of best security practice is that you must always assume that your users are lazy, stupid, hostile or insane -- and design accordingly. Unfortunately, many operations omit this either because they don't want to face this unfortunate reality, or because they don't find it politically correct, or because they want to pretend that their users are magically different from everyone else's users. We see the results of this on a daily basis via forums like DataLoss, yet few modify their procedures as a result.
[ link to this | view in chronology ]
Re: Why bother hacking code...
[ link to this | view in chronology ]
Re: Why bother hacking code...
[ link to this | view in chronology ]
Re: Re: Why bother hacking code...
Can remember running a standard off the shelf password cracker on the user database a number of years ago for an organisation I worked for. Within 10 minutes it had 80% of the passwords (~200 users) and less than 3% lasted the 12 hour run (unsuprisingly mostly the IT dept passwords). On the strength of that I managed to insist on password strength limitations being implemented, but even then it took serious arguing to not have that rolled back when the users started complaining.
[ link to this | view in chronology ]
It also worked for Twitter, Orkut and any other service that uses emails for the creation of accounts.
You wouldn't believe how many people let those email accounts expire by not logging into them :)
[ link to this | view in chronology ]
Re:
User:
- Use email managers that logs into it automatically.
Company:
- Send users an email every 3 months and only let them login after they click on the email sent, so the account is never expired. With an explanation of why that happens and encourage users to use some sort of email manager with a full tutorial on how to set up one.
[ link to this | view in chronology ]
Re: Re:
Oh, and using a mail client that logs in automatically? Thanks. That'll make it much easier to grab user/password pairs from their (probably) unencrypted POP and IMAP sessions.
[ link to this | view in chronology ]
Re: Re: Re:
[ link to this | view in chronology ]
Re: Re: Re: Re:
Then three of the users wondered how they had their identities stolen and why the computer got cracked into and the main hard drive thrashed a month after they got it!
Excuse? "Easy to remember" of course and being a church just who would want to crack it?
When I recovered the drive it had been acting as a seed for porn, and various forms of "piracy" which might explain the calls from the ISP about using way, way too much bandwidth.
Some of them hate me now because they're now restricted to passwords of 10 characters that have to use numbers, mixed case, special characters AND can survive a basic dictionary attack.
It's not that they're nitwits, it's just that their naieve and can't imagine why anyone would do THAT to a church computer.
[ link to this | view in chronology ]
Re: Re: Re:
POP and IMAP today are almost all encrypted by SSL, so how exactly somebody would sniff out those user/passwords?
Unless people are using their own email servers that are configured not to use any form off secure channel.
[ link to this | view in chronology ]
[ link to this | view in chronology ]
Re:
[ link to this | view in chronology ]
Re:
Well, shit. The reality I've been fed is far better than the reality I've led.
[ link to this | view in chronology ]
Re: "War Games"
[ link to this | view in chronology ]
Re: Re: "War Games"
I still like this movie, but even when I watched it, I knew how unrealistic it was. An acoustical modem might be able to dial the phone using touch-tone, but it can't hang up. There was no standard that would allow a terminal program to display hi-res graphics sent from a computer mainframe. No computer simply uses a password to login, without also needing a user name. Two different computer system wouldn't have exactly the same speech synthesizer. No code can be cracked one digit at at time, if it could, any code could be cracked in a matter of seconds. Even using random characters as opposed to cycling through the entire ASCII character set in sequence, it would only take the average computer of the time less than 30 seconds to crack the code. No computer accepts a numeric argument by spelling out the word.
I'm letting the AI of the computer slide, because that was the main plot device of the movie.
[ link to this | view in chronology ]
Re: Re: Re: "War Games"
the SID chip...
Yes it could produce the exact same voice as wargames (within reason, some words had to be typed different for the 'text to speech' to make the right sounds).
The sound capabilites of that machine were way beyond it's time...
[ link to this | view in chronology ]
What I didn't get
[ link to this | view in chronology ]
Re: actually
[ link to this | view in chronology ]
[ link to this | view in chronology ]
Re:
[ link to this | view in chronology ]
[ link to this | view in chronology ]
Computers beep as they print inch-tall letters to the screen.
All error messages flash in giant letters, locking the entire computer.
Any GUI operation can be accomplished by simply typing furiously on the keyboard.
You can plug in a USB flash drive and it will instantly take over the entire computer without ever running any software and can download gigabytes of data in seconds.
Any photo, no matter how low the resolution, can be "cleaned up" into a crystal clear, 10-megapixel image.
Any password can be "hacked" by simply typing furiously on the keyboard.
Computers can be set to erase the hard drive if you don't enter the right password and there is absolutely no way to prevent this, even if the hard drive is hooked to another computer system as a slave drive.
Any data on a hard drive can be undeleted, even to the point where a decade worth of use can be recovered despite being overwritten dozens of times.
Hard drives are like the warehouse at the end of Raiders of the Lost Ark, where files can be hidden away and it can take days or even weeks of digging to uncover them.
Clear panes of glass make great monitors and it's not all distracting to be able to see through them to everything that's happening in the distance.
Any computer system can instantly overlay any image or window on top of any other window, and it will be perfectly positioned without the user ever having to manually reposition it.
All video chat systems are capable of sending full-screen video at 30 FPS, even over a WiFi connection.
All software works on all computers regardless of the age or model of the computer.
All third person video games allow you to control every individual muscle on your character, making it possible to perform any movement that you can do in real life.
[ link to this | view in chronology ]
Re:
[ link to this | view in chronology ]
Re:
I'm not anything like an expert at coding nor a particularly adept computer user and your list of movie liberties is spot on even for me. Heck, my standards for reality are so low I appreciate shows where a someone uses a mouse or a window opens with no audible fanfare whatsoever.
Love the exciting music montages of people searching the internet...cause that is some heart-pounding stuff! The intense faces bathed in electric glow and suspenseful music tells me so!
Sit still, Imagunna hack you:
*types furiously*
*punches ENTER*
*winds up with paragraph of incomprehensible text*
"His IP has him at Lexington and First! Go, go, go!"
[ link to this | view in chronology ]
Re: Hollywood Computers
Oh, and flashing lights were very popular, too. Even though computers as early as the 1970s no longer had very many of them.
[ link to this | view in chronology ]
[ link to this | view in chronology ]
And what I really like about it is not just that it makes sense, but that she just does it; she doesn't sit around spewing unecessary (and poorly written) exposition for the audience's sake.
[ link to this | view in chronology ]
Re:
There's a reason for that.... the hack is a real SSH exploit!
http://nmap.org/movies.html
[ link to this | view in chronology ]
I got one too
We have our own IT department, there's no need to outsource to some other company when we have our own department. Even if we did, such a thing would go through our IT department, not through the agents. Barking dog in the back yard kind of gave away he's not really at an IT place, he's at his house. Encryption can be tested just fine with out needing to access a special website for the purpose. So many problems with his claim, and that's just off the top of my head. It's a good thing the internet is indeed filtered, or some one with Hollywood knowledge of computing might have fallen for it.
[ link to this | view in chronology ]